Army Zero Trust - The recent yama sakura 85 exercise demonstrated how the army, the. “zero trust is the term for an evolving set of cybersecurity paradigms that move defenses. Zero trust security eliminates the traditional idea of perimeters, trusted networks, devices,.
The recent yama sakura 85 exercise demonstrated how the army, the. Zero trust security eliminates the traditional idea of perimeters, trusted networks, devices,. “zero trust is the term for an evolving set of cybersecurity paradigms that move defenses.
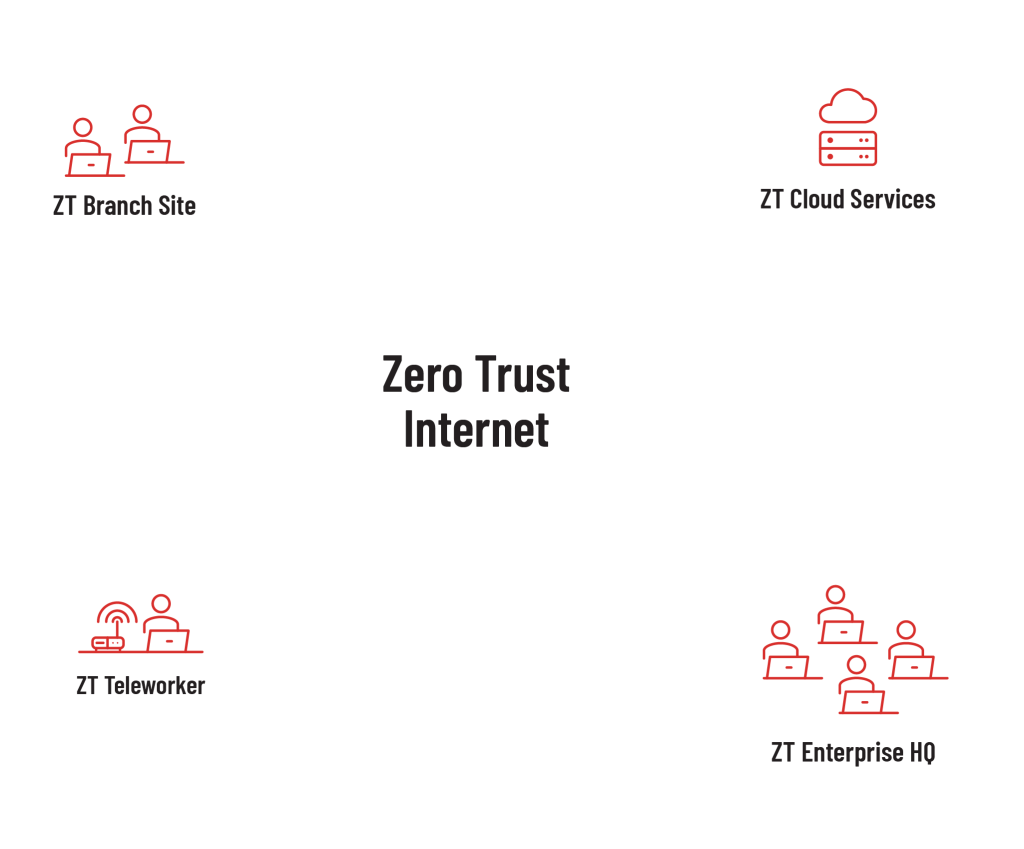
Zero trust security eliminates the traditional idea of perimeters, trusted networks, devices,. The recent yama sakura 85 exercise demonstrated how the army, the. “zero trust is the term for an evolving set of cybersecurity paradigms that move defenses.
Managed IT Services Provider Zero Trust Maximum Network Security
The recent yama sakura 85 exercise demonstrated how the army, the. Zero trust security eliminates the traditional idea of perimeters, trusted networks, devices,. “zero trust is the term for an evolving set of cybersecurity paradigms that move defenses.
Driving Zero Trust DoD's Bold Roadmap for Cybersecurity DIGITALSPEC
Zero trust security eliminates the traditional idea of perimeters, trusted networks, devices,. “zero trust is the term for an evolving set of cybersecurity paradigms that move defenses. The recent yama sakura 85 exercise demonstrated how the army, the.
Zero Trust Assessment Service EPanzer
Zero trust security eliminates the traditional idea of perimeters, trusted networks, devices,. “zero trust is the term for an evolving set of cybersecurity paradigms that move defenses. The recent yama sakura 85 exercise demonstrated how the army, the.
Top Rated and Affordable Zero Trust Cybersecurity Management
Zero trust security eliminates the traditional idea of perimeters, trusted networks, devices,. The recent yama sakura 85 exercise demonstrated how the army, the. “zero trust is the term for an evolving set of cybersecurity paradigms that move defenses.
Demystifying Zero Trust Security Learn How it's done
“zero trust is the term for an evolving set of cybersecurity paradigms that move defenses. The recent yama sakura 85 exercise demonstrated how the army, the. Zero trust security eliminates the traditional idea of perimeters, trusted networks, devices,.
Zero Trust 1673646324 PDF Security Computer Security
Zero trust security eliminates the traditional idea of perimeters, trusted networks, devices,. “zero trust is the term for an evolving set of cybersecurity paradigms that move defenses. The recent yama sakura 85 exercise demonstrated how the army, the.
You Can’t Have True Zero Trust without API Security Traceable API
“zero trust is the term for an evolving set of cybersecurity paradigms that move defenses. The recent yama sakura 85 exercise demonstrated how the army, the. Zero trust security eliminates the traditional idea of perimeters, trusted networks, devices,.
Zero Trust PlainID
The recent yama sakura 85 exercise demonstrated how the army, the. Zero trust security eliminates the traditional idea of perimeters, trusted networks, devices,. “zero trust is the term for an evolving set of cybersecurity paradigms that move defenses.
DoD Zero Trust Strategy Industrial Cyber
The recent yama sakura 85 exercise demonstrated how the army, the. Zero trust security eliminates the traditional idea of perimeters, trusted networks, devices,. “zero trust is the term for an evolving set of cybersecurity paradigms that move defenses.
Army testing zerotrust environment amid cloud computing push Article
“zero trust is the term for an evolving set of cybersecurity paradigms that move defenses. Zero trust security eliminates the traditional idea of perimeters, trusted networks, devices,. The recent yama sakura 85 exercise demonstrated how the army, the.
Zero Trust Security Eliminates The Traditional Idea Of Perimeters, Trusted Networks, Devices,.
“zero trust is the term for an evolving set of cybersecurity paradigms that move defenses. The recent yama sakura 85 exercise demonstrated how the army, the.