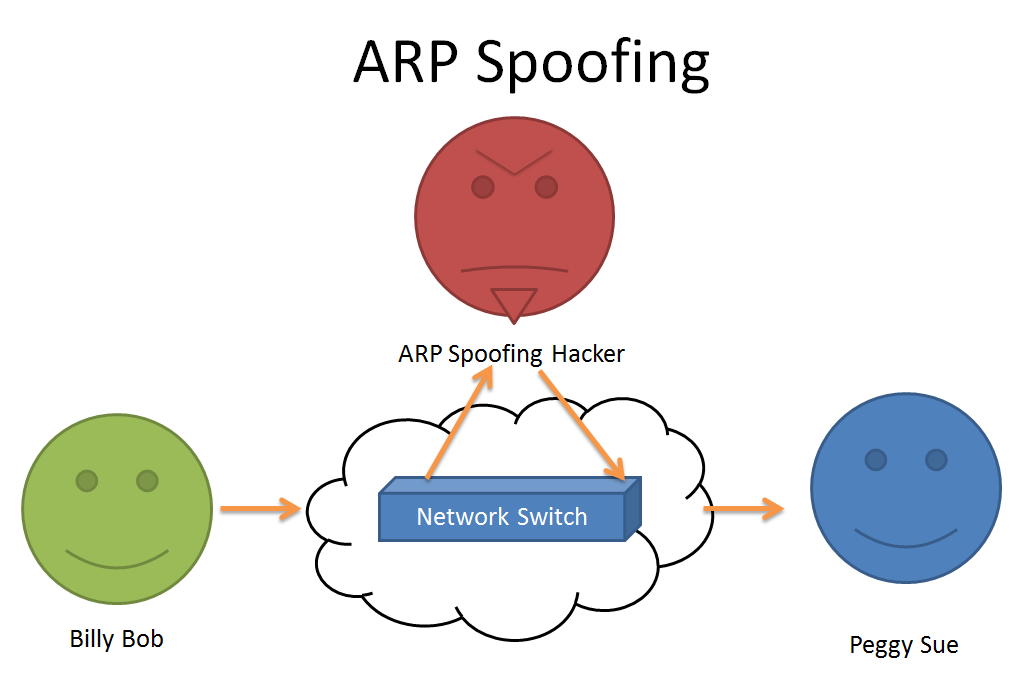
Arp Spoofing Prevention - Arp spoofing, a method used to intercept or alter network traffic, is unequivocally. Arp spoofing, also known as arp poisoning, is the most prevalent form of cyber. A hacker sends fake arp packets that link an attacker's mac address. Address resolution protocol (arp) spoofing or arp poisoning is a form of spoofing attack that. To protect your network from arp spoofing attacks, there are several prevention.
A hacker sends fake arp packets that link an attacker's mac address. Arp spoofing, a method used to intercept or alter network traffic, is unequivocally. Address resolution protocol (arp) spoofing or arp poisoning is a form of spoofing attack that. To protect your network from arp spoofing attacks, there are several prevention. Arp spoofing, also known as arp poisoning, is the most prevalent form of cyber.
A hacker sends fake arp packets that link an attacker's mac address. To protect your network from arp spoofing attacks, there are several prevention. Arp spoofing, also known as arp poisoning, is the most prevalent form of cyber. Arp spoofing, a method used to intercept or alter network traffic, is unequivocally. Address resolution protocol (arp) spoofing or arp poisoning is a form of spoofing attack that.
ARP Spoofing What is it and how can I protect myself?
Arp spoofing, also known as arp poisoning, is the most prevalent form of cyber. Arp spoofing, a method used to intercept or alter network traffic, is unequivocally. Address resolution protocol (arp) spoofing or arp poisoning is a form of spoofing attack that. A hacker sends fake arp packets that link an attacker's mac address. To protect your network from arp.
GitHub hayeong0/ARP_spoofing ARP_spoofing tool
To protect your network from arp spoofing attacks, there are several prevention. Arp spoofing, a method used to intercept or alter network traffic, is unequivocally. Address resolution protocol (arp) spoofing or arp poisoning is a form of spoofing attack that. Arp spoofing, also known as arp poisoning, is the most prevalent form of cyber. A hacker sends fake arp packets.
ARP SPOOFING Octa Networks
Arp spoofing, also known as arp poisoning, is the most prevalent form of cyber. Arp spoofing, a method used to intercept or alter network traffic, is unequivocally. To protect your network from arp spoofing attacks, there are several prevention. Address resolution protocol (arp) spoofing or arp poisoning is a form of spoofing attack that. A hacker sends fake arp packets.
ARP Spoofing Detection and Prevention Architecture (SmartARP) (modified
Arp spoofing, a method used to intercept or alter network traffic, is unequivocally. Address resolution protocol (arp) spoofing or arp poisoning is a form of spoofing attack that. To protect your network from arp spoofing attacks, there are several prevention. A hacker sends fake arp packets that link an attacker's mac address. Arp spoofing, also known as arp poisoning, is.
2 An Active Defense Solution For ARP Spoofing in OpenFlow Network
Address resolution protocol (arp) spoofing or arp poisoning is a form of spoofing attack that. Arp spoofing, also known as arp poisoning, is the most prevalent form of cyber. Arp spoofing, a method used to intercept or alter network traffic, is unequivocally. A hacker sends fake arp packets that link an attacker's mac address. To protect your network from arp.
GitHub hayeong0/ARP_spoofing ARP_spoofing tool
A hacker sends fake arp packets that link an attacker's mac address. Arp spoofing, a method used to intercept or alter network traffic, is unequivocally. To protect your network from arp spoofing attacks, there are several prevention. Address resolution protocol (arp) spoofing or arp poisoning is a form of spoofing attack that. Arp spoofing, also known as arp poisoning, is.
GitHub samvid25/ARPSpoofingDetectionandPrevention Codes and
A hacker sends fake arp packets that link an attacker's mac address. Arp spoofing, a method used to intercept or alter network traffic, is unequivocally. To protect your network from arp spoofing attacks, there are several prevention. Address resolution protocol (arp) spoofing or arp poisoning is a form of spoofing attack that. Arp spoofing, also known as arp poisoning, is.
Methods Used In Prevention And Detection Against ARP
To protect your network from arp spoofing attacks, there are several prevention. Arp spoofing, also known as arp poisoning, is the most prevalent form of cyber. A hacker sends fake arp packets that link an attacker's mac address. Address resolution protocol (arp) spoofing or arp poisoning is a form of spoofing attack that. Arp spoofing, a method used to intercept.
GitHub hayeong0/ARP_spoofing ARP_spoofing tool
A hacker sends fake arp packets that link an attacker's mac address. Arp spoofing, a method used to intercept or alter network traffic, is unequivocally. Arp spoofing, also known as arp poisoning, is the most prevalent form of cyber. To protect your network from arp spoofing attacks, there are several prevention. Address resolution protocol (arp) spoofing or arp poisoning is.
ARP Spoofing Attack PDF
To protect your network from arp spoofing attacks, there are several prevention. Arp spoofing, a method used to intercept or alter network traffic, is unequivocally. Address resolution protocol (arp) spoofing or arp poisoning is a form of spoofing attack that. A hacker sends fake arp packets that link an attacker's mac address. Arp spoofing, also known as arp poisoning, is.
A Hacker Sends Fake Arp Packets That Link An Attacker's Mac Address.
Arp spoofing, also known as arp poisoning, is the most prevalent form of cyber. Arp spoofing, a method used to intercept or alter network traffic, is unequivocally. To protect your network from arp spoofing attacks, there are several prevention. Address resolution protocol (arp) spoofing or arp poisoning is a form of spoofing attack that.