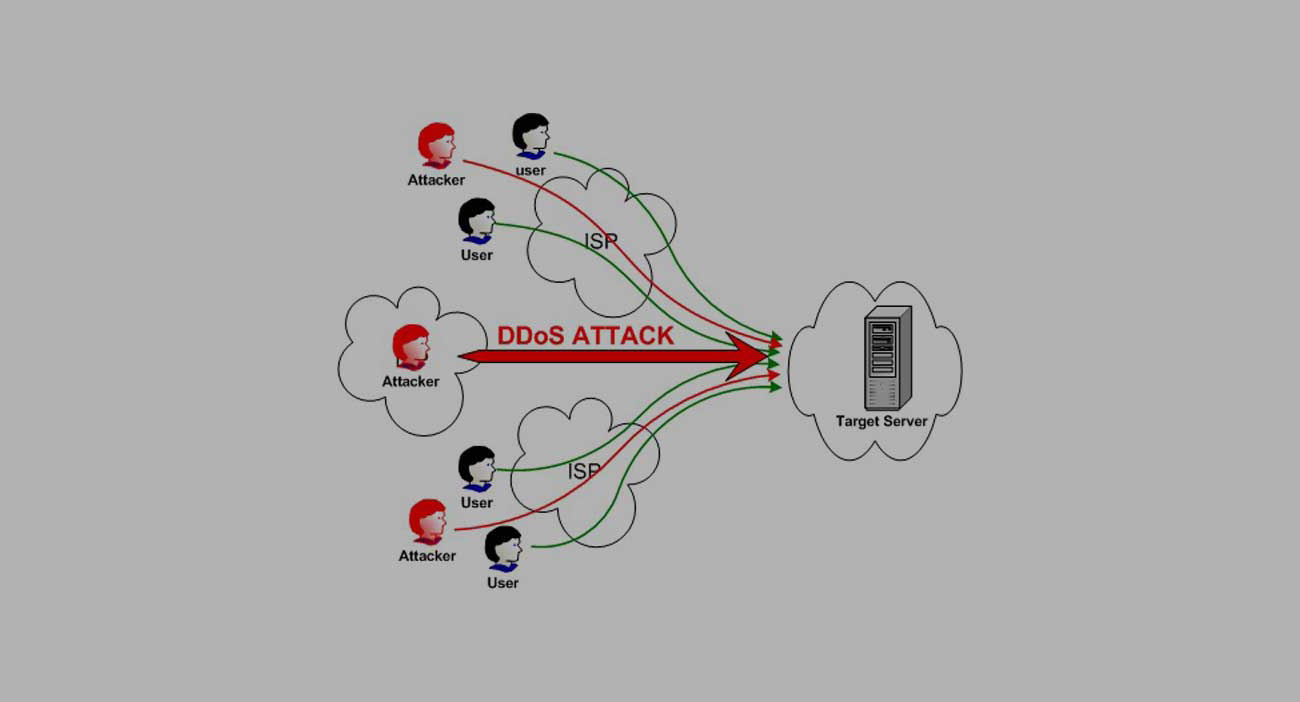
Dos Attack Prevention - Their purpose is to disrupt an organization’s. It uses the seven osi model and focuses three main attack. In a ddos attack, numerous malicious external systems work in. What is denial of service attack. Denial of service (dos) attacks focus on making a machine or network resource unavailable, utilizing methods like traffic flooding, or exploiting vulnerabilities to disrupt services. In this tutorial, we will introduce you to what denial of service attack is, how it is performed and how you can protect against such attacks.
In a ddos attack, numerous malicious external systems work in. Denial of service (dos) attacks focus on making a machine or network resource unavailable, utilizing methods like traffic flooding, or exploiting vulnerabilities to disrupt services. What is denial of service attack. Their purpose is to disrupt an organization’s. In this tutorial, we will introduce you to what denial of service attack is, how it is performed and how you can protect against such attacks. It uses the seven osi model and focuses three main attack.
What is denial of service attack. Their purpose is to disrupt an organization’s. In a ddos attack, numerous malicious external systems work in. In this tutorial, we will introduce you to what denial of service attack is, how it is performed and how you can protect against such attacks. Denial of service (dos) attacks focus on making a machine or network resource unavailable, utilizing methods like traffic flooding, or exploiting vulnerabilities to disrupt services. It uses the seven osi model and focuses three main attack.
DoS attack and prevention module of the proposed model Download
Their purpose is to disrupt an organization’s. In a ddos attack, numerous malicious external systems work in. Denial of service (dos) attacks focus on making a machine or network resource unavailable, utilizing methods like traffic flooding, or exploiting vulnerabilities to disrupt services. What is denial of service attack. It uses the seven osi model and focuses three main attack.
The proposed methodology to detect DoS attack. Download Scientific
Denial of service (dos) attacks focus on making a machine or network resource unavailable, utilizing methods like traffic flooding, or exploiting vulnerabilities to disrupt services. In this tutorial, we will introduce you to what denial of service attack is, how it is performed and how you can protect against such attacks. It uses the seven osi model and focuses three.
(PDF) DoS Attack Prevention Technique in Wireless Sensor Networks
It uses the seven osi model and focuses three main attack. Denial of service (dos) attacks focus on making a machine or network resource unavailable, utilizing methods like traffic flooding, or exploiting vulnerabilities to disrupt services. In this tutorial, we will introduce you to what denial of service attack is, how it is performed and how you can protect against.
What Is a Denial of Service (DoS) Attack? Dr. Ware Technology
In a ddos attack, numerous malicious external systems work in. What is denial of service attack. In this tutorial, we will introduce you to what denial of service attack is, how it is performed and how you can protect against such attacks. Denial of service (dos) attacks focus on making a machine or network resource unavailable, utilizing methods like traffic.
PPT DoS attacks prevention PowerPoint Presentation, free download
What is denial of service attack. In this tutorial, we will introduce you to what denial of service attack is, how it is performed and how you can protect against such attacks. It uses the seven osi model and focuses three main attack. Denial of service (dos) attacks focus on making a machine or network resource unavailable, utilizing methods like.
"Dos Attack" and How To Protect from a Dos Attack Informainzo
What is denial of service attack. It uses the seven osi model and focuses three main attack. Their purpose is to disrupt an organization’s. In a ddos attack, numerous malicious external systems work in. In this tutorial, we will introduce you to what denial of service attack is, how it is performed and how you can protect against such attacks.
Denial of service (DoS) attack. The Official Website of The
What is denial of service attack. Their purpose is to disrupt an organization’s. In this tutorial, we will introduce you to what denial of service attack is, how it is performed and how you can protect against such attacks. In a ddos attack, numerous malicious external systems work in. It uses the seven osi model and focuses three main attack.
Dos Attack (3 PDF PDF Denial Of Service Attack Security
Denial of service (dos) attacks focus on making a machine or network resource unavailable, utilizing methods like traffic flooding, or exploiting vulnerabilities to disrupt services. What is denial of service attack. Their purpose is to disrupt an organization’s. In a ddos attack, numerous malicious external systems work in. In this tutorial, we will introduce you to what denial of service.
Schematic diagram of the strategy of DoS attack detection and
In a ddos attack, numerous malicious external systems work in. In this tutorial, we will introduce you to what denial of service attack is, how it is performed and how you can protect against such attacks. What is denial of service attack. It uses the seven osi model and focuses three main attack. Their purpose is to disrupt an organization’s.
Denial of Service (DoS) Attack Types and Prevention
Their purpose is to disrupt an organization’s. Denial of service (dos) attacks focus on making a machine or network resource unavailable, utilizing methods like traffic flooding, or exploiting vulnerabilities to disrupt services. In this tutorial, we will introduce you to what denial of service attack is, how it is performed and how you can protect against such attacks. It uses.
It Uses The Seven Osi Model And Focuses Three Main Attack.
Their purpose is to disrupt an organization’s. In a ddos attack, numerous malicious external systems work in. Denial of service (dos) attacks focus on making a machine or network resource unavailable, utilizing methods like traffic flooding, or exploiting vulnerabilities to disrupt services. What is denial of service attack.