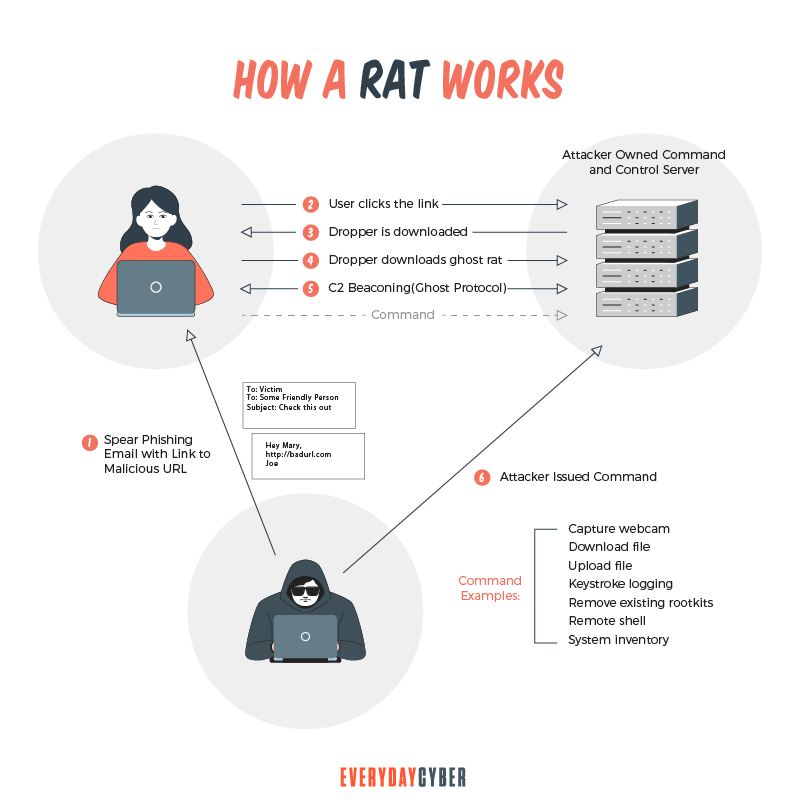
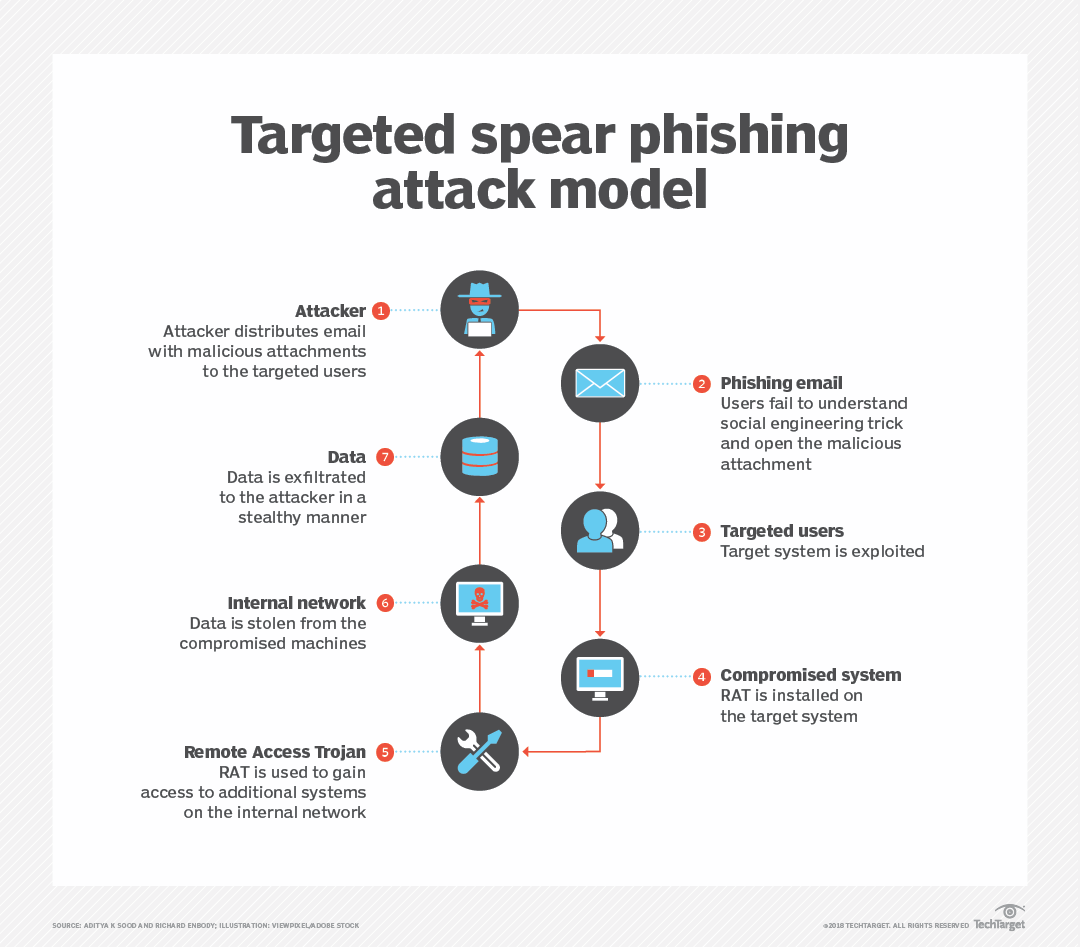
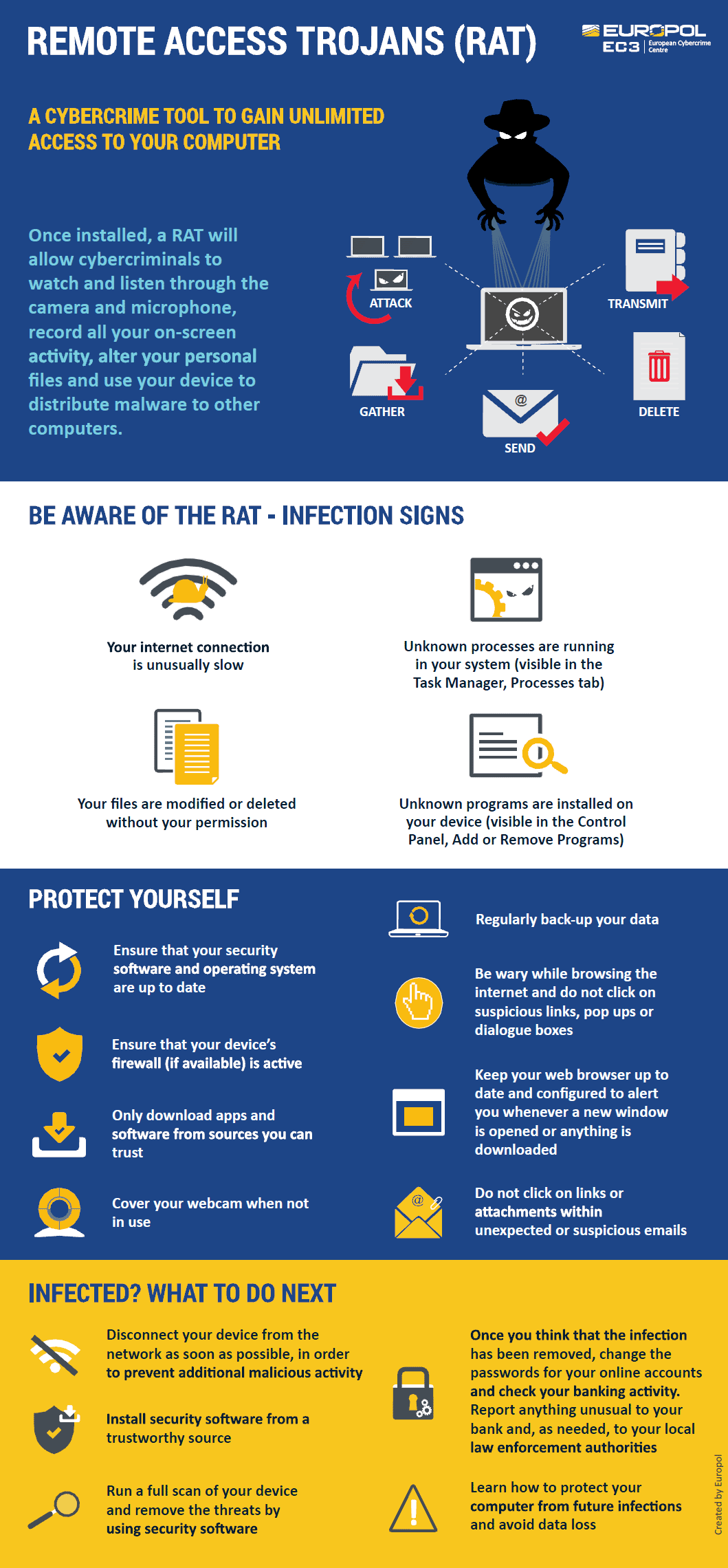
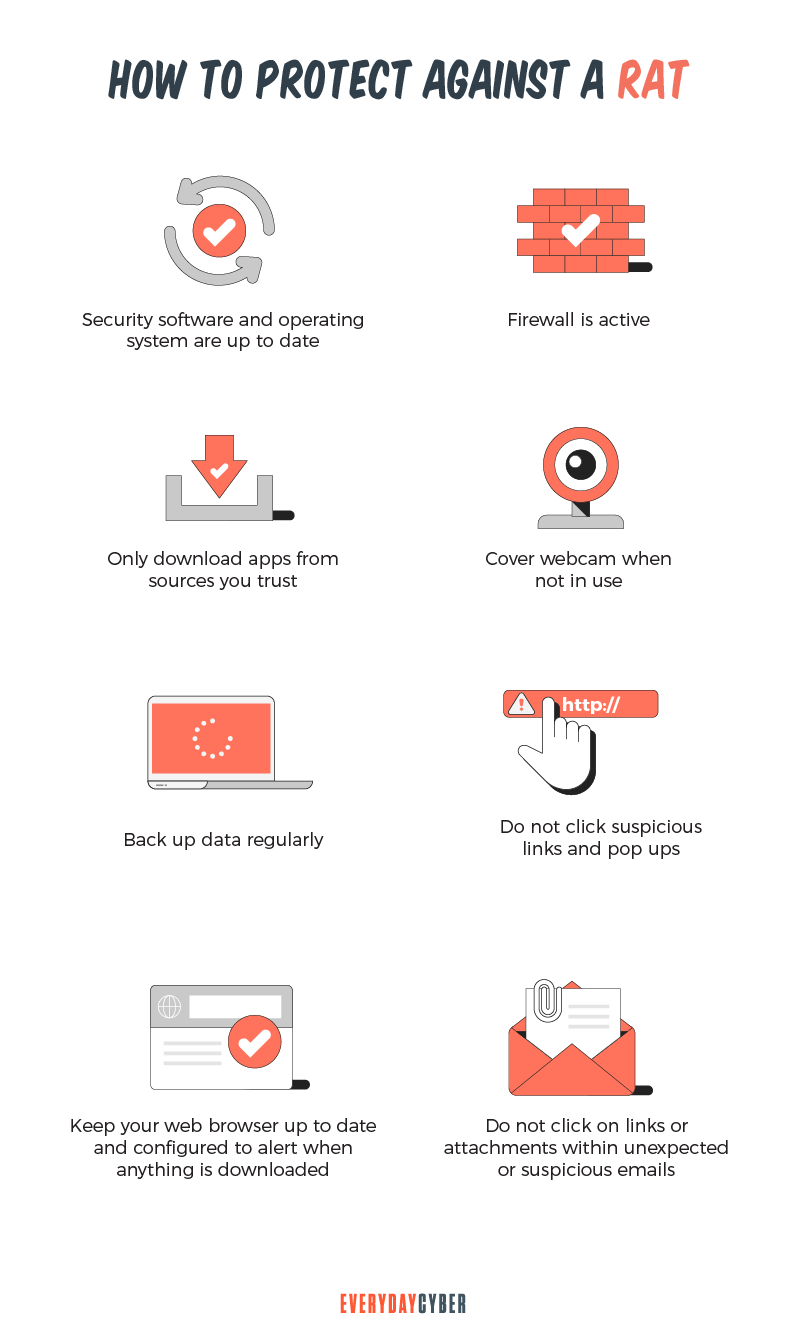
How To Prevent A Rat Trojan - As a rat gets administrative privileges on the infected computer, it can exploit that to control the microphone or webcam of. Preventing remote access trojan attacks requires a combination of cybersecurity best practices, including using strong.
Preventing remote access trojan attacks requires a combination of cybersecurity best practices, including using strong. As a rat gets administrative privileges on the infected computer, it can exploit that to control the microphone or webcam of.
Preventing remote access trojan attacks requires a combination of cybersecurity best practices, including using strong. As a rat gets administrative privileges on the infected computer, it can exploit that to control the microphone or webcam of.
What is Remote Access Trojan (RAT) Detection and Removal
Preventing remote access trojan attacks requires a combination of cybersecurity best practices, including using strong. As a rat gets administrative privileges on the infected computer, it can exploit that to control the microphone or webcam of.
RAT Trojan Access Remote Pentestmag
As a rat gets administrative privileges on the infected computer, it can exploit that to control the microphone or webcam of. Preventing remote access trojan attacks requires a combination of cybersecurity best practices, including using strong.
What is Remote Access Trojan (RAT) Zerosuniverse
Preventing remote access trojan attacks requires a combination of cybersecurity best practices, including using strong. As a rat gets administrative privileges on the infected computer, it can exploit that to control the microphone or webcam of.
GitHub NMan1/RATTrojan Advanced Remote Access Trojan & Server
Preventing remote access trojan attacks requires a combination of cybersecurity best practices, including using strong. As a rat gets administrative privileges on the infected computer, it can exploit that to control the microphone or webcam of.
Rat Trojan
As a rat gets administrative privileges on the infected computer, it can exploit that to control the microphone or webcam of. Preventing remote access trojan attacks requires a combination of cybersecurity best practices, including using strong.
What is a Remote Access Trojan (RAT)? EveryDayCyber
As a rat gets administrative privileges on the infected computer, it can exploit that to control the microphone or webcam of. Preventing remote access trojan attacks requires a combination of cybersecurity best practices, including using strong.
What is a RAT (Remote Access Trojan)? Definition from TechTarget
As a rat gets administrative privileges on the infected computer, it can exploit that to control the microphone or webcam of. Preventing remote access trojan attacks requires a combination of cybersecurity best practices, including using strong.
Glossary Remote Access Trojan (RAT) Banyan Security
Preventing remote access trojan attacks requires a combination of cybersecurity best practices, including using strong. As a rat gets administrative privileges on the infected computer, it can exploit that to control the microphone or webcam of.
How To Prevent Trojan Virus Sellsense23
Preventing remote access trojan attacks requires a combination of cybersecurity best practices, including using strong. As a rat gets administrative privileges on the infected computer, it can exploit that to control the microphone or webcam of.
Preventing Remote Access Trojan Attacks Requires A Combination Of Cybersecurity Best Practices, Including Using Strong.
As a rat gets administrative privileges on the infected computer, it can exploit that to control the microphone or webcam of.