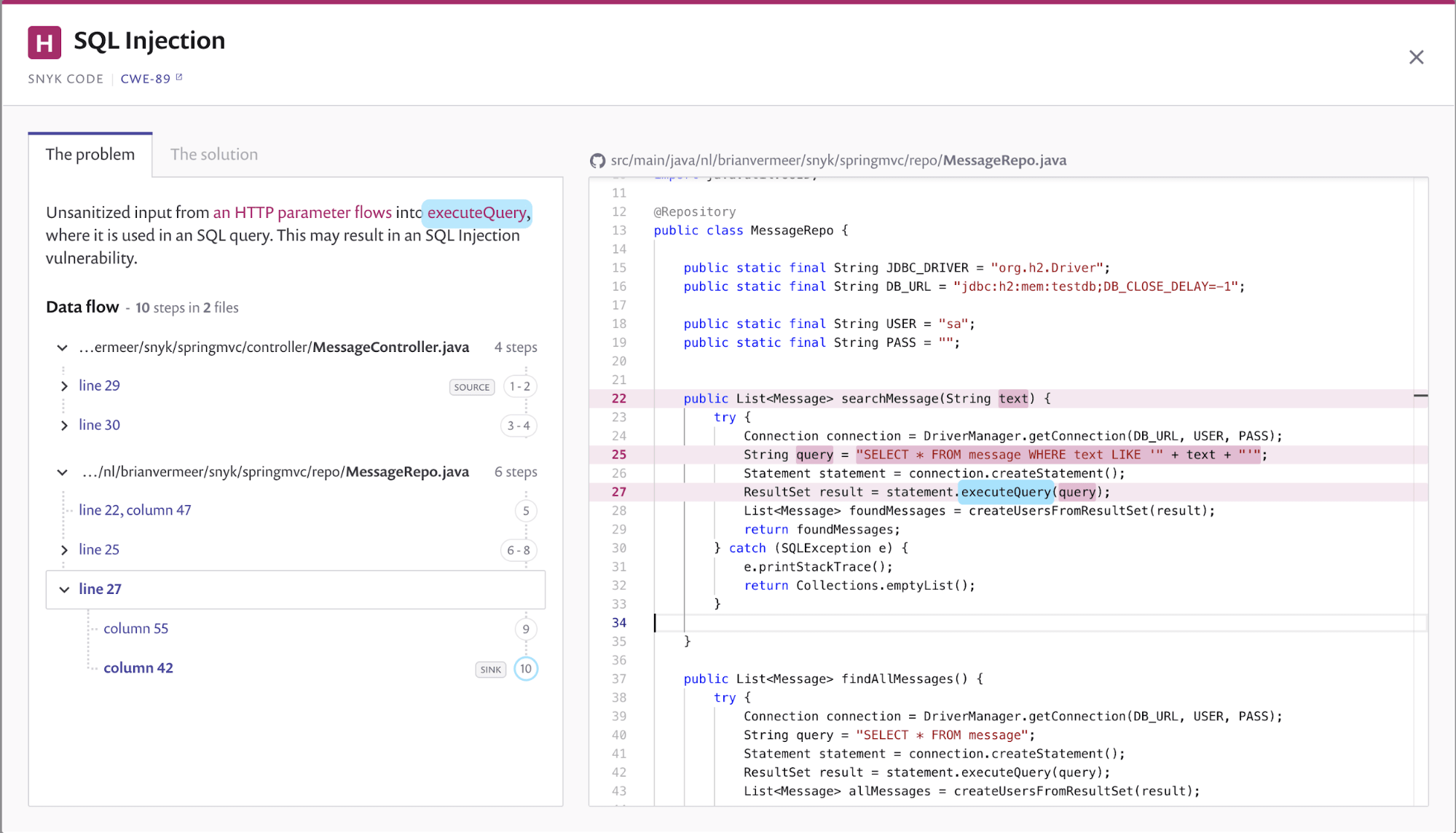
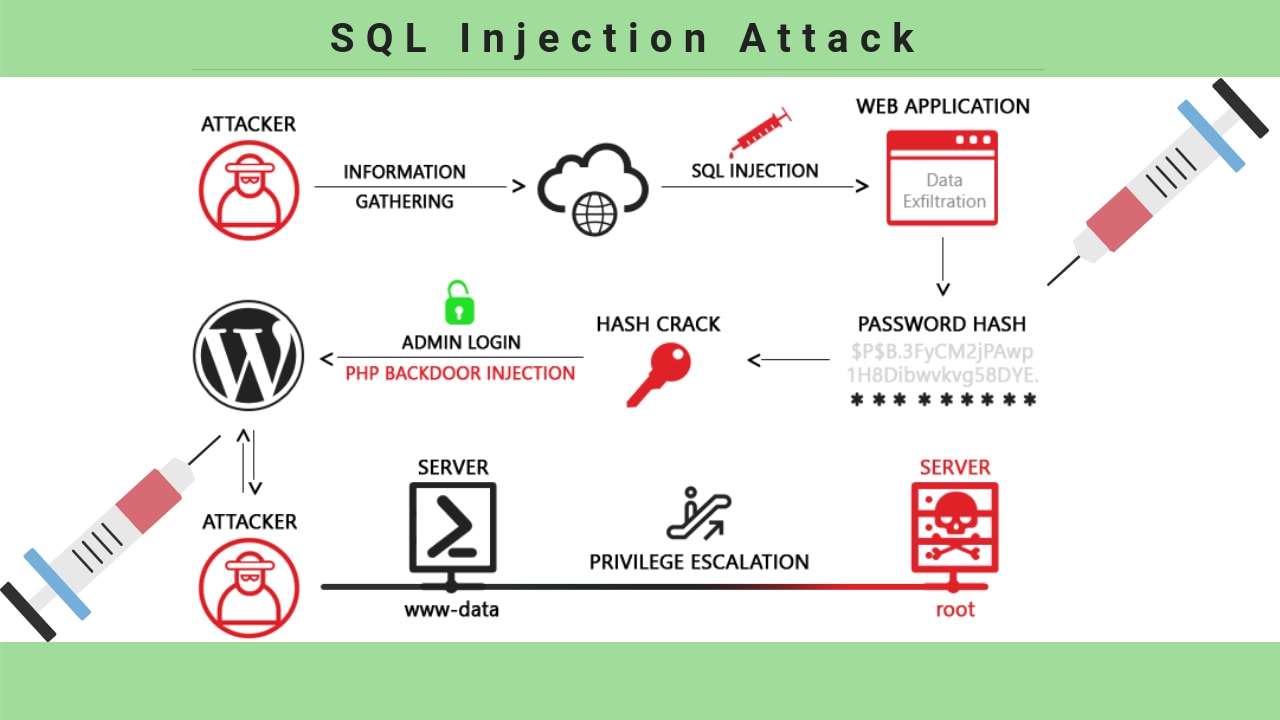
How To Prevent An Sql Injection Attack - The following six methods offer a comprehensive defense against these threats, highlighting how to prevent sql injection. Developers can prevent sql injection vulnerabilities in web applications by utilizing parameterized database queries with bound,. When using dynamic sql within a stored procedure, the application must properly sanitize the user input to eliminate the risk of code.
Developers can prevent sql injection vulnerabilities in web applications by utilizing parameterized database queries with bound,. When using dynamic sql within a stored procedure, the application must properly sanitize the user input to eliminate the risk of code. The following six methods offer a comprehensive defense against these threats, highlighting how to prevent sql injection.
When using dynamic sql within a stored procedure, the application must properly sanitize the user input to eliminate the risk of code. The following six methods offer a comprehensive defense against these threats, highlighting how to prevent sql injection. Developers can prevent sql injection vulnerabilities in web applications by utilizing parameterized database queries with bound,.
How to Prevent SQL Injection Attacks PreEmptive
The following six methods offer a comprehensive defense against these threats, highlighting how to prevent sql injection. Developers can prevent sql injection vulnerabilities in web applications by utilizing parameterized database queries with bound,. When using dynamic sql within a stored procedure, the application must properly sanitize the user input to eliminate the risk of code.
SQL Injection Attack Types, Examples and Prevention
When using dynamic sql within a stored procedure, the application must properly sanitize the user input to eliminate the risk of code. The following six methods offer a comprehensive defense against these threats, highlighting how to prevent sql injection. Developers can prevent sql injection vulnerabilities in web applications by utilizing parameterized database queries with bound,.
How to Prevent a SQL Injection Attack? Loginworks Softwares
Developers can prevent sql injection vulnerabilities in web applications by utilizing parameterized database queries with bound,. When using dynamic sql within a stored procedure, the application must properly sanitize the user input to eliminate the risk of code. The following six methods offer a comprehensive defense against these threats, highlighting how to prevent sql injection.
How to Prevent SQL Injection Examples of SQL Attacks Electric
Developers can prevent sql injection vulnerabilities in web applications by utilizing parameterized database queries with bound,. When using dynamic sql within a stored procedure, the application must properly sanitize the user input to eliminate the risk of code. The following six methods offer a comprehensive defense against these threats, highlighting how to prevent sql injection.
SQL Injection Types, Examples And Prevention, 49 OFF
Developers can prevent sql injection vulnerabilities in web applications by utilizing parameterized database queries with bound,. When using dynamic sql within a stored procedure, the application must properly sanitize the user input to eliminate the risk of code. The following six methods offer a comprehensive defense against these threats, highlighting how to prevent sql injection.
How To Prevent Sql Code Injection Attacks Ademploy19
When using dynamic sql within a stored procedure, the application must properly sanitize the user input to eliminate the risk of code. The following six methods offer a comprehensive defense against these threats, highlighting how to prevent sql injection. Developers can prevent sql injection vulnerabilities in web applications by utilizing parameterized database queries with bound,.
How to Prevent SQL Injection Programming Cube
The following six methods offer a comprehensive defense against these threats, highlighting how to prevent sql injection. Developers can prevent sql injection vulnerabilities in web applications by utilizing parameterized database queries with bound,. When using dynamic sql within a stored procedure, the application must properly sanitize the user input to eliminate the risk of code.
What Is Sql Injection How To Prevent Sql Injection Attack In Php Mysql
When using dynamic sql within a stored procedure, the application must properly sanitize the user input to eliminate the risk of code. The following six methods offer a comprehensive defense against these threats, highlighting how to prevent sql injection. Developers can prevent sql injection vulnerabilities in web applications by utilizing parameterized database queries with bound,.
What Is SQL Injection Attack? Cloud WAF
The following six methods offer a comprehensive defense against these threats, highlighting how to prevent sql injection. When using dynamic sql within a stored procedure, the application must properly sanitize the user input to eliminate the risk of code. Developers can prevent sql injection vulnerabilities in web applications by utilizing parameterized database queries with bound,.
SQL Injection Prevention How It Works & How to Prevent It Parasoft
When using dynamic sql within a stored procedure, the application must properly sanitize the user input to eliminate the risk of code. The following six methods offer a comprehensive defense against these threats, highlighting how to prevent sql injection. Developers can prevent sql injection vulnerabilities in web applications by utilizing parameterized database queries with bound,.
Developers Can Prevent Sql Injection Vulnerabilities In Web Applications By Utilizing Parameterized Database Queries With Bound,.
When using dynamic sql within a stored procedure, the application must properly sanitize the user input to eliminate the risk of code. The following six methods offer a comprehensive defense against these threats, highlighting how to prevent sql injection.