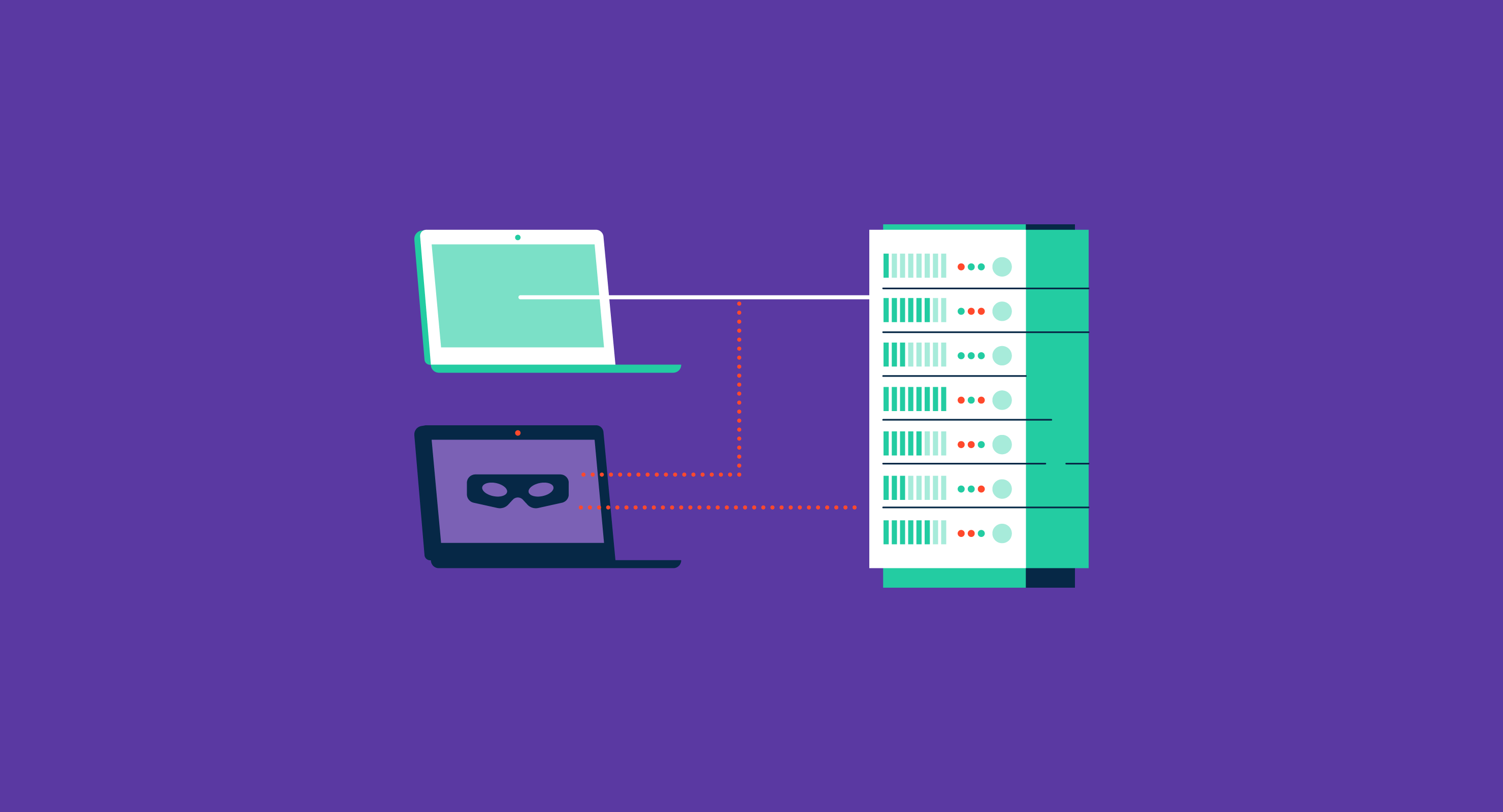
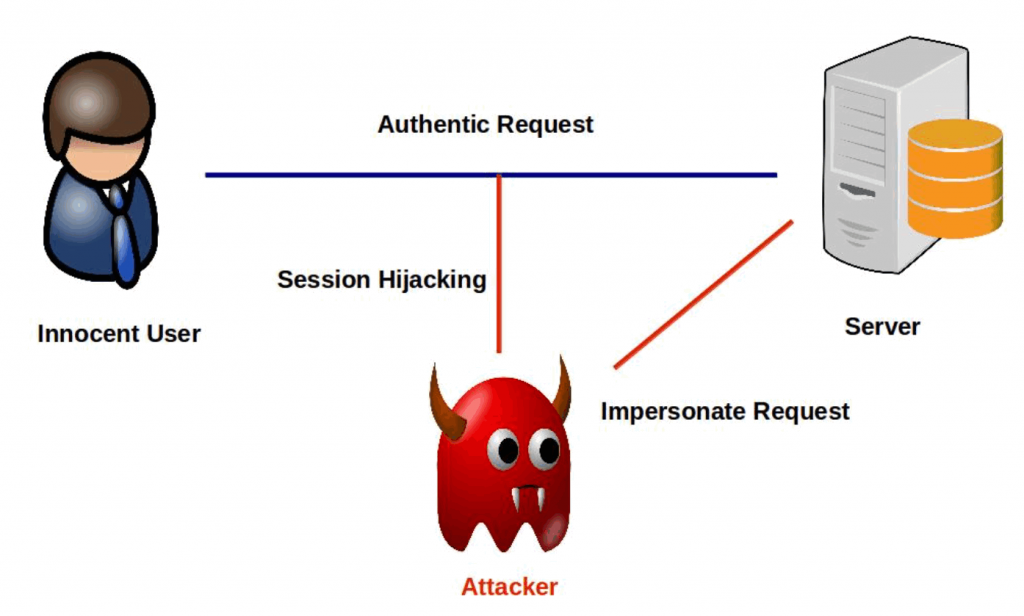
How To Prevent Session Hijacking - Session hijacking involves an attacker using captured, brute forced or reverse. Learn about session hijacking, detection methods, and prevention techniques. To prevent session hijacking using the session id, you can store a hashed string inside the.
To prevent session hijacking using the session id, you can store a hashed string inside the. Learn about session hijacking, detection methods, and prevention techniques. Session hijacking involves an attacker using captured, brute forced or reverse.
Learn about session hijacking, detection methods, and prevention techniques. To prevent session hijacking using the session id, you can store a hashed string inside the. Session hijacking involves an attacker using captured, brute forced or reverse.
What Is Session Hijacking and How Can You Prevent It?
Session hijacking involves an attacker using captured, brute forced or reverse. Learn about session hijacking, detection methods, and prevention techniques. To prevent session hijacking using the session id, you can store a hashed string inside the.
How to Prevent Session Hijacking Logix Consulting Managed IT Support
Learn about session hijacking, detection methods, and prevention techniques. To prevent session hijacking using the session id, you can store a hashed string inside the. Session hijacking involves an attacker using captured, brute forced or reverse.
Configuring Session Hijacking Protection PDF Http Cookie Proxy Server
To prevent session hijacking using the session id, you can store a hashed string inside the. Learn about session hijacking, detection methods, and prevention techniques. Session hijacking involves an attacker using captured, brute forced or reverse.
Prevent Session Hijacking.pdf Transmission Control Protocol Network
Session hijacking involves an attacker using captured, brute forced or reverse. To prevent session hijacking using the session id, you can store a hashed string inside the. Learn about session hijacking, detection methods, and prevention techniques.
How to Prevent Session Hijacking? Baeldung on Computer Science
Learn about session hijacking, detection methods, and prevention techniques. To prevent session hijacking using the session id, you can store a hashed string inside the. Session hijacking involves an attacker using captured, brute forced or reverse.
Session Hijacking Attack, Example and Prevention
Session hijacking involves an attacker using captured, brute forced or reverse. Learn about session hijacking, detection methods, and prevention techniques. To prevent session hijacking using the session id, you can store a hashed string inside the.
How Sessions Hijacking leaves you Vulnerable to Theft
Session hijacking involves an attacker using captured, brute forced or reverse. To prevent session hijacking using the session id, you can store a hashed string inside the. Learn about session hijacking, detection methods, and prevention techniques.
Don't Gamble with Security Session Hijacking Risks
Learn about session hijacking, detection methods, and prevention techniques. To prevent session hijacking using the session id, you can store a hashed string inside the. Session hijacking involves an attacker using captured, brute forced or reverse.
What Is Session Hijacking? How to Ensure Session Privacy
To prevent session hijacking using the session id, you can store a hashed string inside the. Session hijacking involves an attacker using captured, brute forced or reverse. Learn about session hijacking, detection methods, and prevention techniques.
To Prevent Session Hijacking Using The Session Id, You Can Store A Hashed String Inside The.
Learn about session hijacking, detection methods, and prevention techniques. Session hijacking involves an attacker using captured, brute forced or reverse.