Prevent Ic Card To Be Copied - If the encryption scheme were cracked, you could clone these tags as well and send the correct key using a cloned card. Some cards are inherently insecure because they use weak encryption (such as the mifare cards often used in transit systems.). Here is a summary of the technologies and how they can bolster building security and reduce the chances of card cloning: There are two common ways to prevent tampering in nfc cards:
Some cards are inherently insecure because they use weak encryption (such as the mifare cards often used in transit systems.). If the encryption scheme were cracked, you could clone these tags as well and send the correct key using a cloned card. There are two common ways to prevent tampering in nfc cards: Here is a summary of the technologies and how they can bolster building security and reduce the chances of card cloning:
If the encryption scheme were cracked, you could clone these tags as well and send the correct key using a cloned card. Here is a summary of the technologies and how they can bolster building security and reduce the chances of card cloning: Some cards are inherently insecure because they use weak encryption (such as the mifare cards often used in transit systems.). There are two common ways to prevent tampering in nfc cards:
Yanzeo RFID Shielded Sleeve Card Blocking 13.56mhz IC card Protection
Here is a summary of the technologies and how they can bolster building security and reduce the chances of card cloning: If the encryption scheme were cracked, you could clone these tags as well and send the correct key using a cloned card. Some cards are inherently insecure because they use weak encryption (such as the mifare cards often used.
Radio Frequency Identification Card Reader 13.56Mhz Type C IC Card
If the encryption scheme were cracked, you could clone these tags as well and send the correct key using a cloned card. Some cards are inherently insecure because they use weak encryption (such as the mifare cards often used in transit systems.). There are two common ways to prevent tampering in nfc cards: Here is a summary of the technologies.
Ic ID Card Non Contact USB DrivE Free NFC Door Access Card Reader (13
If the encryption scheme were cracked, you could clone these tags as well and send the correct key using a cloned card. Here is a summary of the technologies and how they can bolster building security and reduce the chances of card cloning: There are two common ways to prevent tampering in nfc cards: Some cards are inherently insecure because.
30 pcs/set Credit Card Protector Sleeves RFID 13.56mhz IC card
Here is a summary of the technologies and how they can bolster building security and reduce the chances of card cloning: If the encryption scheme were cracked, you could clone these tags as well and send the correct key using a cloned card. Some cards are inherently insecure because they use weak encryption (such as the mifare cards often used.
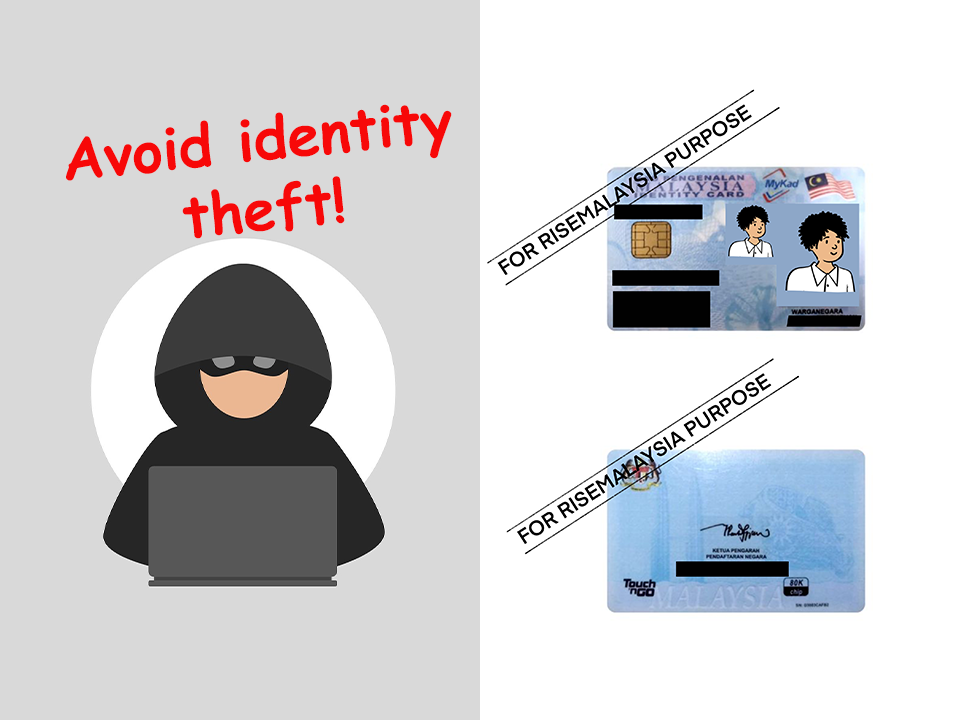
How And Why To Cross Your IC Photocopy To Avoid Identity Theft
There are two common ways to prevent tampering in nfc cards: Some cards are inherently insecure because they use weak encryption (such as the mifare cards often used in transit systems.). If the encryption scheme were cracked, you could clone these tags as well and send the correct key using a cloned card. Here is a summary of the technologies.
MCTCIC Elevator IC Access Control System Elevator IC Card AFLY
If the encryption scheme were cracked, you could clone these tags as well and send the correct key using a cloned card. Here is a summary of the technologies and how they can bolster building security and reduce the chances of card cloning: Some cards are inherently insecure because they use weak encryption (such as the mifare cards often used.
GitHub ALGER0221/RFIDICcardcopydevice this black box can easy
If the encryption scheme were cracked, you could clone these tags as well and send the correct key using a cloned card. Some cards are inherently insecure because they use weak encryption (such as the mifare cards often used in transit systems.). Here is a summary of the technologies and how they can bolster building security and reduce the chances.
IC card icon. Contactless payment method. Vector. 26729969 Vector Art
Here is a summary of the technologies and how they can bolster building security and reduce the chances of card cloning: There are two common ways to prevent tampering in nfc cards: Some cards are inherently insecure because they use weak encryption (such as the mifare cards often used in transit systems.). If the encryption scheme were cracked, you could.
IC Card Reader Cleaning Cards » Marco
There are two common ways to prevent tampering in nfc cards: If the encryption scheme were cracked, you could clone these tags as well and send the correct key using a cloned card. Here is a summary of the technologies and how they can bolster building security and reduce the chances of card cloning: Some cards are inherently insecure because.
IC card for fuel dispenser from China manufacturer Ecotec
Here is a summary of the technologies and how they can bolster building security and reduce the chances of card cloning: Some cards are inherently insecure because they use weak encryption (such as the mifare cards often used in transit systems.). There are two common ways to prevent tampering in nfc cards: If the encryption scheme were cracked, you could.
Here Is A Summary Of The Technologies And How They Can Bolster Building Security And Reduce The Chances Of Card Cloning:
Some cards are inherently insecure because they use weak encryption (such as the mifare cards often used in transit systems.). There are two common ways to prevent tampering in nfc cards: If the encryption scheme were cracked, you could clone these tags as well and send the correct key using a cloned card.