Regex Sql Injection Prevention - Generally sql injection occurs in the strings passed to the parameters of a sql command such as insert, update, delete, or select. However, you could enter a very long. Sql injection is a vulnerability and threat, with the most occurrence in a web based system. Search, filter and view user submitted regular expressions in the regex library. Over 20,000 entries, and counting! This cheat sheet will help you prevent sql injection flaws in your applications. No, your application will not be 100% secured if you use some pattern matching or regex to identify sql injection attack. It will define what sql injection is, explain where those. You can't invoke a command from a regex, so you can't do an sql injection in this case. The regular expression threat protection policy can protect your backend apis and microservices from sql injection attacks.
This cheat sheet will help you prevent sql injection flaws in your applications. In this research we evaluate and. Over 20,000 entries, and counting! However, you could enter a very long. Search, filter and view user submitted regular expressions in the regex library. No, your application will not be 100% secured if you use some pattern matching or regex to identify sql injection attack. You can't invoke a command from a regex, so you can't do an sql injection in this case. Sql injection is a vulnerability and threat, with the most occurrence in a web based system. Generally sql injection occurs in the strings passed to the parameters of a sql command such as insert, update, delete, or select. The regular expression threat protection policy can protect your backend apis and microservices from sql injection attacks.
Search, filter and view user submitted regular expressions in the regex library. This cheat sheet will help you prevent sql injection flaws in your applications. You can't invoke a command from a regex, so you can't do an sql injection in this case. The regular expression threat protection policy can protect your backend apis and microservices from sql injection attacks. No, your application will not be 100% secured if you use some pattern matching or regex to identify sql injection attack. Sql injection is a vulnerability and threat, with the most occurrence in a web based system. However, you could enter a very long. It will define what sql injection is, explain where those. In this research we evaluate and. Over 20,000 entries, and counting!
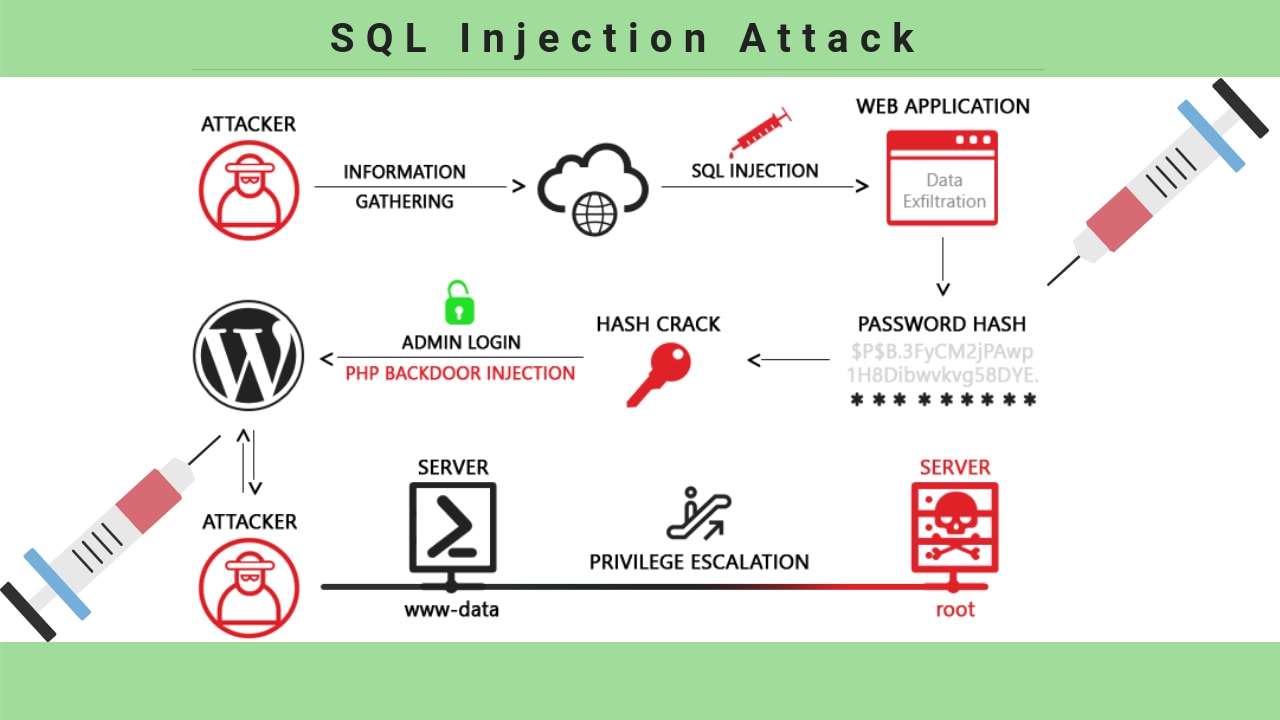
SQL Injection Attack Definition, Types & Prevention
You can't invoke a command from a regex, so you can't do an sql injection in this case. Over 20,000 entries, and counting! No, your application will not be 100% secured if you use some pattern matching or regex to identify sql injection attack. In this research we evaluate and. This cheat sheet will help you prevent sql injection flaws.
What is SQL Injection? Attack Example & Prevention Gridinsoft
In this research we evaluate and. No, your application will not be 100% secured if you use some pattern matching or regex to identify sql injection attack. Over 20,000 entries, and counting! This cheat sheet will help you prevent sql injection flaws in your applications. Sql injection is a vulnerability and threat, with the most occurrence in a web based.
SQL Injection Types, Examples And Prevention, 49 OFF
Generally sql injection occurs in the strings passed to the parameters of a sql command such as insert, update, delete, or select. However, you could enter a very long. No, your application will not be 100% secured if you use some pattern matching or regex to identify sql injection attack. The regular expression threat protection policy can protect your backend.
Types of SQL Injection Attack Examples Gridinsoft Blogs
In this research we evaluate and. Over 20,000 entries, and counting! Search, filter and view user submitted regular expressions in the regex library. This cheat sheet will help you prevent sql injection flaws in your applications. However, you could enter a very long.
GitHub banulalakwindu/sqlinjectionpreventionguide A practical
It will define what sql injection is, explain where those. Over 20,000 entries, and counting! Sql injection is a vulnerability and threat, with the most occurrence in a web based system. This cheat sheet will help you prevent sql injection flaws in your applications. No, your application will not be 100% secured if you use some pattern matching or regex.
SQL Injection Types, Examples And Prevention, 49 OFF
The regular expression threat protection policy can protect your backend apis and microservices from sql injection attacks. Sql injection is a vulnerability and threat, with the most occurrence in a web based system. No, your application will not be 100% secured if you use some pattern matching or regex to identify sql injection attack. Over 20,000 entries, and counting! Generally.
SQL Injection More Command PDF
You can't invoke a command from a regex, so you can't do an sql injection in this case. This cheat sheet will help you prevent sql injection flaws in your applications. Search, filter and view user submitted regular expressions in the regex library. Generally sql injection occurs in the strings passed to the parameters of a sql command such as.
An InDepth Guide to Preventing SQL Injection Attacks Through Prepared
This cheat sheet will help you prevent sql injection flaws in your applications. It will define what sql injection is, explain where those. You can't invoke a command from a regex, so you can't do an sql injection in this case. The regular expression threat protection policy can protect your backend apis and microservices from sql injection attacks. Over 20,000.
6 Expert Tips on SQL Injection Mitigation & Prevention Enterprise
It will define what sql injection is, explain where those. Search, filter and view user submitted regular expressions in the regex library. Sql injection is a vulnerability and threat, with the most occurrence in a web based system. In this research we evaluate and. However, you could enter a very long.
SQL Injection Prevention 7 Tested Ways
Generally sql injection occurs in the strings passed to the parameters of a sql command such as insert, update, delete, or select. Over 20,000 entries, and counting! However, you could enter a very long. Search, filter and view user submitted regular expressions in the regex library. In this research we evaluate and.
You Can't Invoke A Command From A Regex, So You Can't Do An Sql Injection In This Case.
Generally sql injection occurs in the strings passed to the parameters of a sql command such as insert, update, delete, or select. Sql injection is a vulnerability and threat, with the most occurrence in a web based system. No, your application will not be 100% secured if you use some pattern matching or regex to identify sql injection attack. Search, filter and view user submitted regular expressions in the regex library.
It Will Define What Sql Injection Is, Explain Where Those.
The regular expression threat protection policy can protect your backend apis and microservices from sql injection attacks. However, you could enter a very long. In this research we evaluate and. This cheat sheet will help you prevent sql injection flaws in your applications.